SQL injection is a technique where malicious users can inject SQL commands into an SQL statement, via web page input. Injected SQL commands can alter SQL statement and compromise the security of a web application.

JSON stands for JavaScript Object Notation. JSON objects are used for transferring data

Two commonly used methods for a request-response between a client and server are: GET and POST.
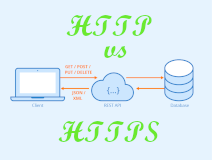
Hypertext Transfer Protocol - No Data Encryption
The Hypertext Transfer Protocol (HTTP) is an application-level protocol
AOP aims at reducing the amount of "tangled" code by which we mean code that might be implemented in different classes if a OOP language is used but still share important secondary requirements. Such requirements are said to cross-cut the system's basic functionality and are difficult to develop and maintain using non-AOP programming paradigms. Cross-cutting functionality can be thought of as functionality spanning many objects.
Dependency Inversion
The Dependency Inversion Principle states that:
- High level modules should not depend upon low level modules. Both should depend upon abstractions.
- Abstractions should not depend upon details. Details should depend upon abstractions.